Recent searches
Search options
#cryptography
This is a wonderful explainer on zero-knowledge proof/zero-trust verification. So simple, yet so clear.
Guys I've been thinking about this recently
So the telegraph has existed for a while, and became widespread in 1800s. Charles Babbage worked on the first mechanical #computers in the 1820s
What would be the earliest point in time in which a #Bitcoin like #Blockchain could've been made?
As I understand it all the system needs is a #network of computers each running a program that checks for transactions
I'm wondering if a different hash function was used it could be a lot simpler to implement into hardware, but if mechanical computing wasn't powerful enough for that the earliest might've been after WWII with the code breaking machines that the Allies invented
Any boosts would be greatly appreciated!
I discovered this today, I haven't checked it out too much though.
Do not store data in a cloud unless you control the encryption keys.
Constant-Time Code: The Pessimist Case
https://eprint.iacr.org/2025/435
Discussions: https://discu.eu/q/https://eprint.iacr.org/2025/435

As a developer with only enough #cryptography and #CyberSecurity experience to know I don't know enough to trust my own judgements...
If I wanted to add offline functionality to a browser app via PWA mechanisms... (even not offline, local caching to aid performance and save server calls)
Is there anything fundamentally wrong with using the user's password (or some in memory key derived from the password) and web-crypto for the encryption of the data before it goes into local storage?
 @benzogaga33@mamot.fr
@benzogaga33@mamot.frInside the FBI’s Secret Encrypted Phone Company ‘Anom’ https://www.youtube.com/watch?v=uFyk5UOyNqI #cryptography #security
seems my #introduction didn't migrate so here we are.
hello. i used to be on fosstodon at @jabster28@fosstodon.org, but running my own seemed fun so now i'm on my own #sharkey instance at mace.lol
i'm currently in university for a computer science degree (no i won't be homeless.). i do a lot of #programming and like to mess around with general #devops stuff (containerisation and networking mostly) in my free time, a lot of my mini projects revolve around automating this or that and making it work with everything else i have in my own ecosystem.
i #selfhost a lot of services for ephemeral file sharing and password management etc.
my main languages are #javascript / #typescript and #rust but i've been wanting to learn some #cpp or c# recently (i don't always want a program that's 1000% correct, cargo.)
(also css is genuinely an a tier language. insanely fit for purpose.)
i do some #networking and find it pretty fun mostly
i play a lot of #splatoon in my free time. i'm also fond of #mahjong, #minesweeper, and #tetris (modern tetris (usually techmino), not the official app) to sink my time into if i'm on my phone or something.
some more stuff i'm into that's probably more fringe:
#wikipedia editing is pretty fun, though it's rare that i'll get a chance to correct/add to an article that i know about and can source. doing coi requests [en.wikipedia.org] is cool, though, you see some really interesting people
i'd love to be able to do #cooking faster but i feel that's only possible with enough time or money to cook when you don't need to (i have neither)
#libraries are really cool and i'd love to go to more of them and document them. working at one seems fun also
slightly related but i wouldn't mind getting better at #photography at some point (maybe make a pixelfed account?)
my only major political stance on here would probably be that #privacy is a fundamental human right, and a lot of things online right now don't let you control that as well as you should
i guess that leads into me liking #monero, there's not many other ways you can transfer wealth to someone without anyone else snooping. no, b*tcoin doesn't count, it's simply not fit for purpose.
that also goes into #cryptography i suppose. the mathematics inside things like ecdh is pretty beautiful. one of the reasons i'm going to university is to eventually be able to fully understand elliptic curves and a lot of the cryptography we use nowadays.
that's it, thanks for coming to my ted talk. make sure to smash that like button, subscribe, and hit the red bell to get notifications when i upload. also be sure to donate to my patreon and ko-fi, link's in the description. you can also buy the product from this video's spons-
okay i'm done
you should do a random act of kindness today. maybe tomorrow. or not, i'm not your mom.
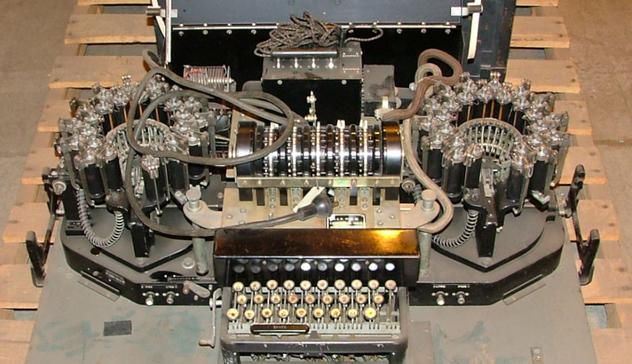
Combined Crypto, Anglo-American Style - If you think about military crypto machines, you probably think about the infamous... - https://hackaday.com/2025/03/06/combined-crypto-anglo-american-style/ #cryptography #history
But cryptography is hard. Until recently, institutions and individuals who need to run #cryptographic operations had to rely on specialists to review the code that their applications is running. Cryptography can protect our privacy and authenticate sources of important information. For #cryptography to work for the people, the people need to understand it.
@grimmauld yes :3
in #cryptography-and-security
 @hacksilon@infosec.exchange
@hacksilon@infosec.exchangeLast week, I finally finished my writeup of a vulnerability based on a misuse of #Cryptography that we found a while back in a penetration test. It's my favorite vulnerability so far, as it relies on abusing basic properties of unauthenticated encryption and shows, in a real-world scenario, how such seemingly theoretical issues can compromise an entire system. In the end, it's a teachable moment about both cryptography and secure software architecture.
I had the draft lying around for more than a year, but reading the articles by @soatok finally reminded me that I should really wrap this up and post it. So, here it is: https://blog.maass.xyz/encryption-isnt-enough-compromising-a-payment-processor-using-math

 @Fiona@blahaj.zone
@Fiona@blahaj.zoneSince I just checked again for a lemmy post and verified that my complaints are still current:
I explicitly recommend against the use of @threemaapp@mastodon.social as a messenger because of their bad #encryption.
I make this recommendation as a professional cryptographer who holds a PhD in that field and give explicit permission to be quoted on it.
The reason for this recommendation is that Threema’s End-to-End encryption offers no forward- or backward secrecy of any kind. This follows directly from the protocol description they themselves publish in their own whitepaper, so if this is a wrong claim, their own publications are wrong, which would be just as much of a reason not to use them!
Any claims about forward-secrecy they make is purely about their transport-layer encryption, which offers zero protection against corrupted servers. If someone corrupts signal’s servers they don’t get anything. If they corrupt Threema’s servers they get everything as ciphertexts that are merely encrypted with a pairwise static key that does not get updated.
A good messenger should not rely on the trustworthiness of the servers, so doing it like that does is not acceptable and enough reason to give the boot to their app.
As much as I dislike its lack of federation (not that Threema is doing any better there), this still means that #Signal remains my recommendation as messenger, with #matrix being an alternative that feels like it makes a degree of sense to me. Other than those two we quickly get into “wouldn’t recommend” territory!
#Threema #itsec #cryptography
does anybody have a good demo library for correctly doing Shamir Secret Sharing?
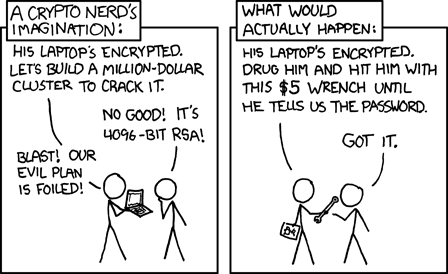
Update: Okay, the best answer so far is this XCKD comic. https://xkcd.com/538/ #encryption #cybersecurity #cryptography