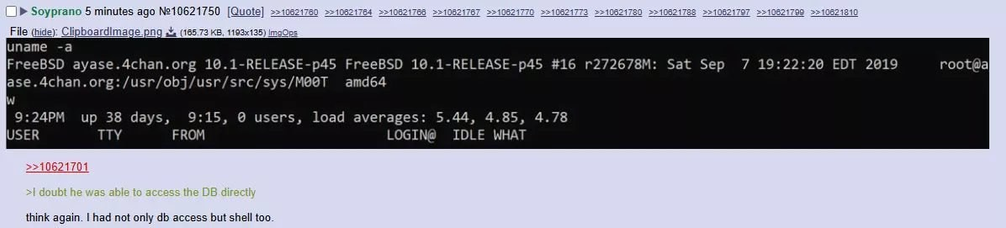
You know when you see news articles about hacks of password databases or critical vulnerabilities in popular software, they usually quote a "CVE" number that officially identified the issue and allowed it to be defined precisely, and tracked? Well that's gone as of today. Looks like the trump regime has cancelled one off the foundational authorities on cybersecurity, the CVE or Common Vulnerabilities and Exposures program, without explanation. Basically the whole of "tech" relies on this, but I guess it's just America supporting the rest of the world, so it has to go. #cybersecurity #cybersec #cve #vulnerability #VulnerabilityDatabase
Edits: typos/autocorrupt







 #
#